Image 1: Imgur.
Image 2: Google Drive png, Google Drive zip.
Image 2 is a recreated copy of image 1, containing different but similar concealed data / file (Same manalink. I aimed to recreate it as best as I could, though it could not be exactly the same). It was recreated at JRP's request to ensure intact data.
The manalink will expire on 6/26/2023 around 4 p.m. PDT.
I only used a ca. 45 kB html script to encrypt and decrypt it.
I have decrypted the image, both by downloading it from the link above and by directly using the link.
I have decrypted it without any Internet connection to confirm that it is possible.
To my knowledge, the decoding process should not involve any word list or keywords.
The concealed data / file is > 100 kB.
This will be my last market using this script. If no one solves it, I will discuss the solution with anyone interested after market close.
M100 reward provided by Marcus Abramovitch. I may provide further rewards for the winner (M150) and contributing commenters (M150 each to JRP and brubsby), depending on how many traders this market gets.
🏅 Top traders
| # | Trader | Total profit |
|---|---|---|
| 1 | Ṁ89 | |
| 2 | Ṁ86 | |
| 3 | Ṁ26 | |
| 4 | Ṁ26 | |
| 5 | Ṁ22 |
People are also trading
Tried a variety of more tools found while searching the web. Aletheia reports a payload of ~11% hiding in the blue channel. Based on my reading so far of the algorithms used by these type of detection tools, I understand these are gross estimates but it is consistent with the visual inspection and with the given information about the challenge (although I suspect it could be hiding in all three channels as well).
I haven't made any further progress; future progress relies on learning/guessing the embedding function used and verifying the result.
I now understand how much these techniques lean on obscurity given how many papers, projects, and variations there are with these algorithms. I underestimated how good the security of these steganographic techniques are even without encryption mechanisms because of the number of variations of techniques that can be applied. Because of this I am selling my YES shares and betting NO since I don't believe it will be solved before the market closes.
The information given about it being performed using HTML and ~ 45 kB was not fruitful in a search for identifying the tool used (I downloaded quite a few repos/npms that met these standards and none of them worked. I also searched for stego with chinese keywords that didn't turn up anything useful either.).
I will post some of my observations and analysis in the hopes it does get solved.
As with the first challenge, the off-shelf suites and tools were not fruitful (including zsteg). If it is hidden within the file structure it is very well hidden, but this is not likely given the following.
Finding the source image through reverse image search, resizing, and then comparing different types of histograms in ImageJ yielded the following two observations:
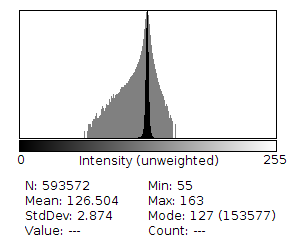
(1) The total count of values in R+B+G for all values looks much higher. (This is very apparent with the Blue channel.)
(2) All the color channel distributions is peaky, as in the previous challenge.
The analysis is conditional on the source image found through reverse search being a good (the correct) comparison to the original file used for hiding the data:
(1) and (2) strongly suggests pixel value alteration. How is it done? Characterizing the changes broadly: dark pixels colors were made darker with the color values also shifted, and lighter pixels were made brighter with the color values also shifted in order to preserve the perceptual brightness and color of the image.
Following from this:
(1) suggests: contrast manipulation, quantization, or some other encoding strategy that produces the same characteristics.
(2) likely suggests contrast manipulation.
From the above assumptions, I assume contrast manipulation is likely the (or one of the) techniques used to hide the data.
@parhizj as with the previous challenge, i also found that resizing a reverse image searched source image never quite fit visually with the steganographic image. with specifically font seeming less "bold". as well as not finding anything with zsteg. so i give the contrast theory credence.
ive also searched the web to a moderate degree for tools similar to the one described to decode it without luck. judging by the author's other social media posts (sorry to snoop) the website or technique might be more prominent in the chinese language steganography sphere, as the encoding method or site seems to have less prominence here, as i haven't found it in my decently broad search. (and it sounds like it's not a truly novel technique)
Here is an image that shows differences in pixel values about a grey value of 127 in comparison to the stock/source image I found.

Histogram intensities of above:
Blue channel histogram of above:
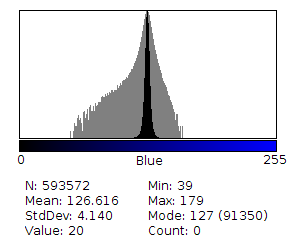
As the blue was changed more than the intensity, this matches the observations yesterday that this likely uses a full color, contrast manipulation method.
@parhizj the concealed data being >100kB leads me to believe it's an image payload and not text, much of the visible intensity change seems like perhaps difference in interpolation method used (as it's mostly around the whiskers) (e.g. nohalo, lohalo, cubic, linear, none, probably more). not really sure where to go from here though.
@brubsby I don't think it's interpolation or compression from looking at how much the color changes, but I could be wrong
@XComhghall if the method injects noise then I would expect no, otherwise maybe? Yes if my assumptions are correct so far
I am paranoid of using ANY "image" hosting websites for images, as they may touch the data file (I don't know what imgur does). Can you provide an additional link to a simple file-sharing type sharing service? Or at least, provide confirmation that you've done a binary diff on the downloaded file from imgur.
@parhizj Yes! I can certainly provide an additional link to a simple file-sharing type sharing service.
Recreated and uploaded to Google Drive. However, I see that /firstuserhere/will-the-mana-link-concealed-within says that Google Drive 'may have done some modifications'. Would you recommend another website or service? I could also upload it to Miraheze. Thanks!
@XComhghall I recommend zipping it and then uploading the zip wherever. That will guarantee they won't compress the image.