Will someone decode this cryptic image by market close (5 p.m. PDT on 6/18)?
I have downloaded the image from both links and decoded it to confirm that it can be decoded. I will compare any solutions to what I decoded.
The first person to decode it will be awarded M100 provided by Marcus Abramovitch. I may further provide a reward (TBD) for the first person who explains how it may be decoded, depending on how many traders this market gets.
🏅 Top traders
| # | Trader | Total profit |
|---|---|---|
| 1 | Ṁ159 | |
| 2 | Ṁ156 | |
| 3 | Ṁ67 | |
| 4 | Ṁ63 | |
| 5 | Ṁ30 |
People are also trading
/XComhghall/challenge-will-someone-claim-the-ma
Last market - Will discuss the solution with anyone interested if this puzzle is not solved.
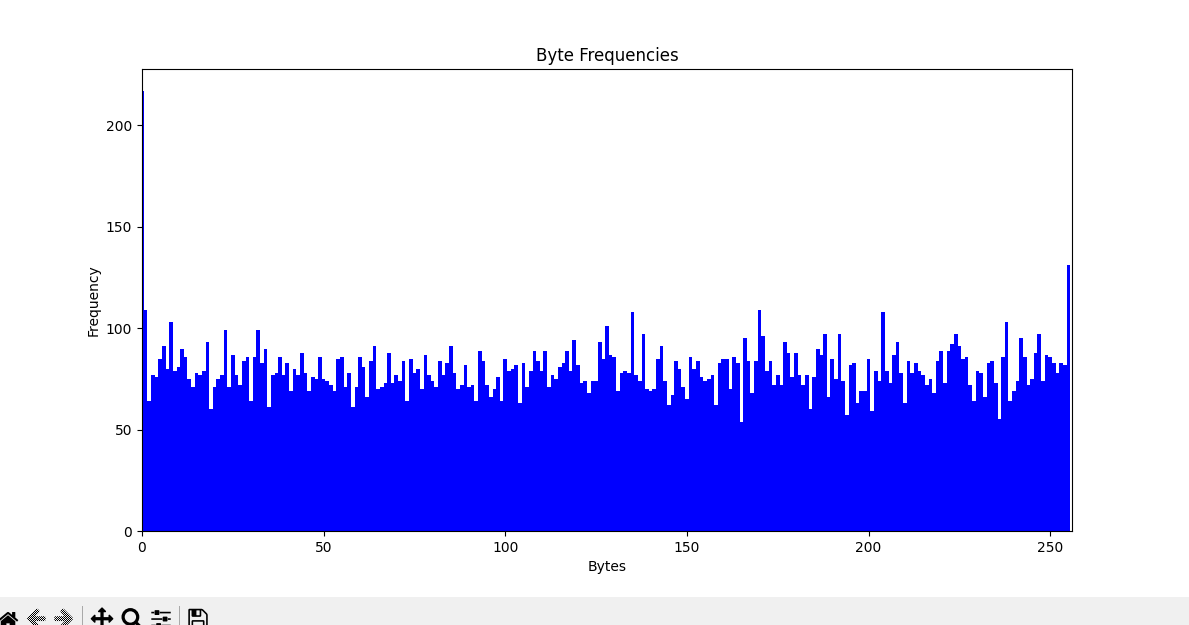
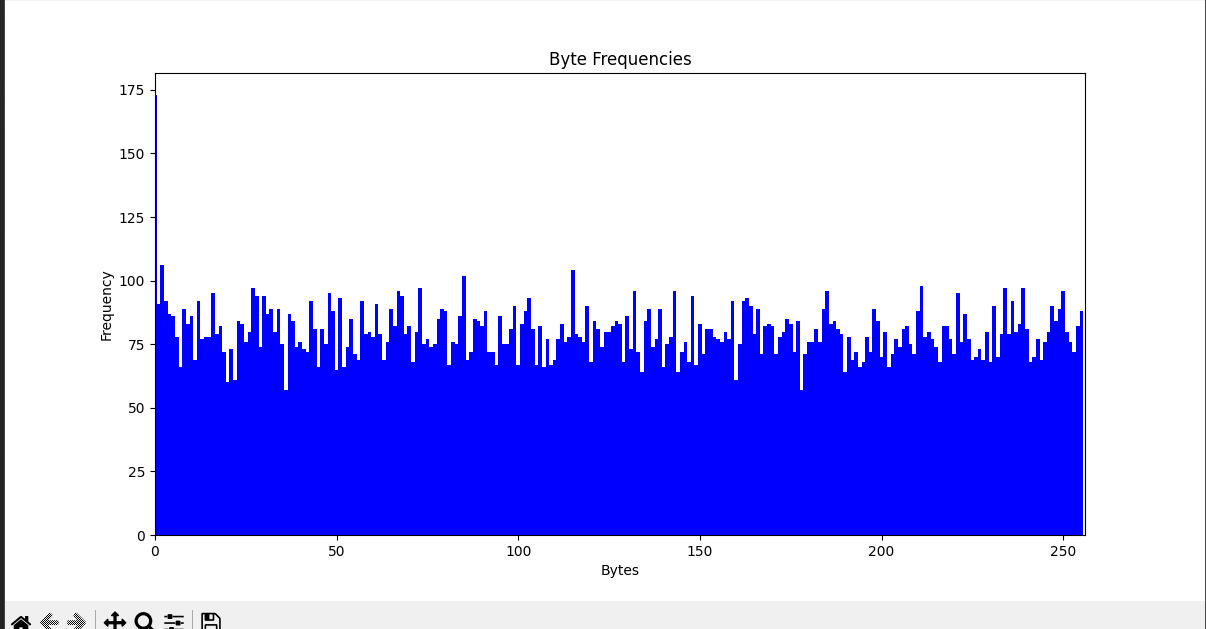
byte frequency from combinations of rgb LSB seems a little too uniform to be the method, ISO-8859-1 decoding seems like mostly mojibake, and no magic number filetype strings found so far.
@brubsby As my car broke down I had some time to work on it this morning and made no progress. I haven't done crypto as a hobby in 20 years so I am out of date; maybe you can point me to some more comprehensive references afterwards. This type of bet is counterproductive at this point to make it a team effort as we've already bet on opposite sides.
As brubsby has claimed he has not solved it with 6 hours left I am increasing my NO bet. I am conditionalising on my guess that brubsby hasn't solved it and won't solve it with 6 hours left.
@brubsby https://gist.github.com/brubsby/1602e38740889fc7cdb79d99c5f4a41f dump of zsteg -a, which i believe identifies filetype magic strings in certain bitmasks of the data, lots of noise but moderately confident a clue is in here
@brubsby Yeah I read about (some of) the current tools. Too much noise to signal from that output (already seen it when I did it a couple days ago)
@brubsby A lot of my funds are all tied up in today's F1 markets at the moment ... I'll check back later when the race is over.
https://manifold.markets/KevinBurke/who-will-come-in-second-place-at-th-81770d62bc19
@parhizj my biggest ledes from zsteg seem to be:
imagedata .. file: SVR2 pure executable (USS/370) - version 117308934
and
b7,rgb,lsb,YX .. zlib: data="wJ7\xA9\xA6\x03\xCBKlA\x9E\xDEt\xBE", offset=238, size=14
which seems to be describing 1. a kind of arcane unix executable when the imagedata itself is run, could very well be noise though, and 2. a zlib archive with the payload "wJ7\xA9\xA6\x03\xCBKlA\x9E\xDEt\xBE", although there was header issues when attempting to decompress it via python zlib, giving this theory a little less credence as well.
not sure what might be implied by not seeing much showing up in the zsteg output, aside from maybe the initial stego being simple and then some unknown (to zsteg) scheme enciphering the bitstream, although I would think if it was a compression algorithm zsteg would find it, and if it was a more difficult scheme it would probably be too hard for this market.
perhaps it's using a key from the link2 market's word list, but i'm not sure how one would begin trying to apply it, as most key based stego tools are only for jpegs. (and funny enough this image has lots of jpeg compression, but is a png, perhaps this is pertinent, but i could not think of a useful manner in which to apply this tidbit)
@brubsby The clue I interpreted was the password might be related to getting around the Chinese firewall so the password would be one of the Chinese banned keywords. This didn't pan out with the only tool I could find that could handle png stego passwords
@parhizj This market, the image, and the encoded information have nothing to do with the market at link 2, except that the image was posted there. To my knowledge, the decoding process should not involve any word list, keywords, or anything specifically related to China.
As I don't have time to solve this stego (I spent an hour trying various common techniques and tools, including using a word list I created from the list of (290+) sensitive words from China (which I thought might be a clue) yet came up empty). If it's a novel technique I don't have the time to discover it, and as no one has posted a proposed solution, I will bet conservatively NO given the market's high percentage.
@parhizj Let me contact you after close on Discord. If no one solves it, I might as well give the M100 to you.
@parhizj Both are the same image. Link 2 links to the comment containing the same image. I have tested it by downloading and decoding the image from both pages. The result is the same.
